With Rapid7's acquisition of the Open Source Pentest tool Metasploit Framework (http://www.metasploit.com)last week. I can't help but as the question; What will happen to it? The folks at Rapid7 assure that the tool will remain free, and will likely improve due to the internal collaboration. I think that they are wanting to find away to creep up on Core Impact (http://www.coresecurity.com), the incredible, but expensive automated pentesting tool. Metasploit has served as a great free option for those who care to spend the time.
What's next; time will only tell...
Cyber Security, Compliance, Security News, Vulnerabilities. Exploits, Tools & Experiences
Tuesday, October 27, 2009
Wednesday, October 21, 2009
Passwords in Log Files
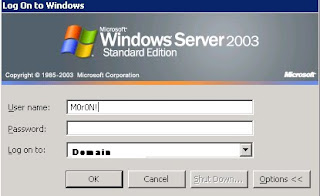
Protect access to your log files. Time and time again, I've conducted penetration test and have gained access to authentication logs on some box along the way. Often times, somewhere in the numerous entries, you'll find someone who has mistakenly entered their password as their username.
Take that user/password gain access to other systems. There is no telling where it can take you.
Tuesday, October 20, 2009
The President on Cyber Security
The President brings attention to the threats of Infomation Warfare and Cyber Crime. Its a good day to be a security professional.
Subscribe to:
Posts (Atom)